Article Published in the Oct 25 Issue of The News Analytics Journal.

Hybrid operations, unlike traditional warfare, bridge martial coercion with non-military measures like sabotage, cyberattack, disinformation, interference in elections, energy blackmail, and weaponised migration. These processes are intentionally vague, cheap but high-impact, allowing state / non-state actors to destabilise their competitors without crossing transparent thresholds.
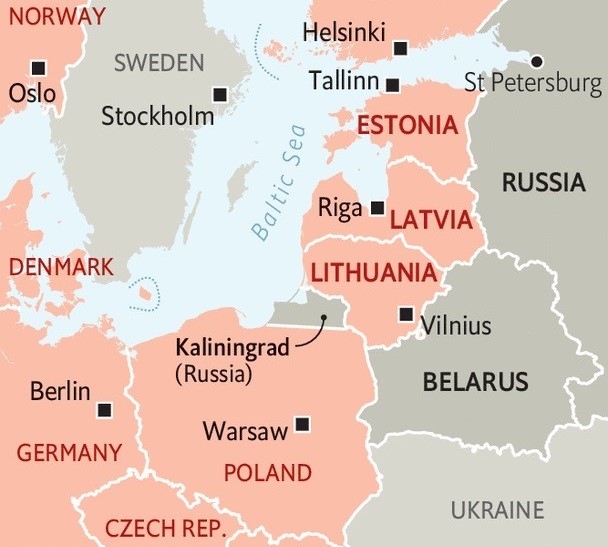
The Russian hybrid war strategy has been a security concern for the Baltic states of Estonia, Latvia, and Lithuania. They are improperly exposed to geography, population, and history relative to Russia. But the danger does not end there in the Baltics: Poland, Finland, and Germany are also at risk from shared energy and digital infrastructure, political interdependence, and disinformation.
Critical infrastructure, notably submarine cables, energy supplies, and digital networks, has also been a key target. With an assault upon such an asset requiring minimal effort but with the ripple effect containing security, economic, and psychological consequences, at least 11 North and Baltic Sea underwater cables have been severed since 2023, both demonstrating the technical possibility and the deniable nature of such an act. This article examines hybrid war strategy across the Baltic states, quantifying regional resiliency and defining policy measures to be taken in defence of their infrastructure.

Hybrid Threats and Activities
Hybrid war threatens Estonia, Latvia, and Lithuania seriously, attacking the cohesion of society, infrastructure, and democratic procedures using methods of sabotage, cyberattacks, disinformation, and disruptions of energy supplies. These are intended to destabilise the Baltic States without triggering traditional war, exploiting vulnerabilities in linked systems.
Information Warfare and Propaganda. Disinformation works extremely well in hybrid warfare, often used through AI-generated content, deepfakes, and tailored social media campaigns on Telegram, TikTok, and local networks. All are designed to produce narratives around specific strategic interests, and linguistic or cultural minorities are the target to be manipulated into divisions. For example, messages can utilise themes of discrimination, nostalgia for the past, or suspicion of international coalition-building. Cultural projects, including patronage of institutions that advance other narratives, can build dual information spaces that undermine social cohesion. Classic cases such as the 2003 Lithuanian presidential foreign-linked funding scandal illustrate how external actors exploit political weaknesses. Current disinformation operations are more likely to derogate support for active conflicts, destabilise international partnership trust, and amplify societal fault lines.
Subversion and Sabotage. Low-tech sabotage can be thoroughly debilitating to social cohesion and infrastructure. For example, the 2024 arson assault on a Vilnius storage facility disclosed weakness in key logistics networks. Likewise, the demolition of historic monuments across regions has been utilised as a means of stirring ethnic or cultural tensions. Deployment of incendiary devices transported through logistics networks in attacks also demonstrates the capabilities for covert disruption. Attacks on key infrastructure, e.g., submarine cables carrying transatlantic communications, financial transactions, and military communications, are conventionally attributed to an accident but cause concern about intentional sabotage. These attacks highlight the asymmetric benefits pursued through precision disruption, taking advantage of vulnerabilities in interdependent systems.
Cyberattacks. Cyber war is a key component of a hybrid strategy, and organisations often conduct distributed denial-of-service (DDoS) attacks on government buildings, energy organisations, and public services. For instance, in 2022, a cyberattack on a Baltic energy organisation disconnected thousands of customers’ services. In showpiece events, as for the 2023 Vilnius NATO Summit, cyberattacks were conducted on public websites and ministries to cause embarrassment and instability.
Espionage. Espionage is used to support these activities, with nationals being said to be recruited to collect intelligence or conduct minor sabotage operations. These activities are intended to erode confidence and destabilise institutions by taking advantage of insider access or local dissatisfaction.
Energy Security Risks. Energy infrastructure is the main target in hybrid warfare as well, and physical and cyberattacks are employed to discredit confidence in alternative energy sources. Diversification policies like Baltic connection to the EU power grid in 2024 or construction of LNG terminals and pipelines have mitigated these risks. Nevertheless, ongoing attacks on critical infrastructure are employed to point towards the long-term problem of safeguarding energy networks against hybrid methods.
Organised Migration. Organised waves of migration, such as the 2021 EU border crisis, demonstrate that humanitarian crises can be manipulated for strategic motives. Migrants from war-torn areas were redirected to border areas, swamping indigenous governments and challenging regional security responses. Such crises are intended to challenge global coalitions and politicise public discussion of migration and security, exerting pressure on governments and societies.
Military Intimidation and Amplification of Support for Hybrid Operations. A display of military strength in strategic regions can serve to enhance hybrid strategies by providing the context of a credible threat. Mass movements, mimicking rapid penetrations into extensive areas of terrain or clandestine activities in border regions, increase tensions and augment the impact of clandestine operations. They capitalise on geographical proximity and cultural ties to vulnerable areas, thereby enhancing the perceived threat of escalation.
Election Interference. Election interference is a popular hybrid method that employs cyberattacks, the leakage of sensitive information, and disinformation as tools to influence public opinion. Social media mobilisation campaigns predicated on the amplification of controversial issues—whether nationalist feelings or ethnic grievances—can influence closely fought elections. They seek to de-legitimise the democratic institutions and undermine those governments amenable to confronting strategic interests.

Preparedness and Reactions of the Baltic States
Despite the seriousness of the threat, the Baltic States have largely been resilient. They have come a long way in countering such vulnerabilities with modernisation, social integration, and neighbourhood cooperation. Investments in energy diversification, for instance, Lithuania’s terminal for liquefied natural gas and Baltic disconnection of old energy grids in 2024, have been curtailing reliance on the outside world. Nevertheless, critical infrastructure such as underwater cables, energy networks, and democratic systems is an attractive target for low-cost, deniable assaults.
Societal and Institutional Resilience. The NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) is hosted by Estonia. Cyber defence and information warfare coordination are instead functions of Lithuania’s National Cyber Security Centre and Latvia’s Strategic Communications Centre of Excellence. Civil defence institutions—such as Estonia’s 15,000-strong National Guard—facilitate rapid mobilisation in times of crisis.
Energy Independence. Integration of the Baltic States’ power grid with European grids, the Świnoujście terminal in Poland, and the Klaipėda LNG terminal are achievements of energy security. These steps limit Moscow’s influence and bolster NATO’s strategic depth.
Integration of Russian speakers. Rights of citizenship have been granted, investments made in learning the Russian language, and the recognition of cultural identities. These steps reduce alienation, but existing tensions between policies of integration and nationalist explanations that emphasise linguistic homogeneity.
Interagency Coordination. Interagency coordination is weak. Border control, crisis management, and intelligence exchange often do not operate in a coordinated manner. Latvia’s border guards, for example, have been criticised compared to more advanced Estonian and Nordic counterparts. NATO and American surveillance capabilities compensate to some extent, but reform at the national level remains to be accomplished.

Strengthening Baltic Defences against Hybrid Threats
Strengthening Baltic defences against hybrid threats involves building inclusive integration, establishing a Comprehensive Resilience Ecosystem (CORE), protecting critical infrastructure, modernising electricity laws, enhancing transparency, and strengthening regional and international cooperation. The following are recommendations:
Facilitate Inclusive Integration. Enlarge programmes to provide equal civic, economic, and political opportunities to cultural and language minorities to build national unity in Estonia, Latvia, and Lithuania.
Envision a Comprehensive Resilience Ecosystem (CORE). Design an integrated system among the defence, cybersecurity, energy, and communications sectors to develop national resilience in the context of hybrid threats, tailored to Baltic priorities and imperatives.
Guard Critical Infrastructure. Prioritise the protection of submarine communications cables and offshore energy installations, taking advantage of regional cooperation in protecting these critical networks.
Modernise Legal Frameworks. Encourage the modernisation of international treaties, such as the UN Convention on the Law of the Sea (UNCLOS), to counter hybrid threats to maritime and critical infrastructure, with the Baltic States coordinating regional action.
Increase Transparency in Deployments. Clearly inform Baltic citizens of regional defence measures to reassure them while dissuading potential aggressors, highlighting national sovereignty.
Upgrade Specialised Forces. Upgrade the Baltic special forces and civilian defence units with assistance from premier intelligence and surveillance capabilities in cooperation with allied countries.
Upgrade Regional Exercises. Regularly conduct exercises such as BALTOPS and Baltic Sentry, which include cyber, maritime, and information warfare exercises, to attain greater readiness and interoperability of the Baltic forces.
Launch Multilingual Campaigns. Develop multiple-language communication strategies to address different communities, counter fake information, and foster social cohesion across Baltic communities.
Enhance Monitoring and Reaction. Collaborate with national cyber units and regional allies to track disinformation in real-time, quickly discredit fakes, and possess a Baltic-led reaction.
Enhance Intelligence Sharing. Enhance Baltic States and European and Indo-Pacific partner cooperation to enhance early warning and reaction to hybrid threats.
Advance Global Norms. Advance global norms to safeguard crucial infrastructure such as submarine cables and cyberspace, and make the Baltic States leaders in securing the global commons.
Conclusion
Defending Estonia, Latvia, and Lithuania against hybrid war is not a regional security problem, but ensuring democratic nations and preserving resilience in a conflict-filled environment that insinuates informational, digital, and physical space. By investing in societal cohesion, infrastructure security, and regional cooperation, the Baltic States can put the solution to hybrid threats and ensure long-term stability.
Please Add Value to the write-up with your views on the subject.
For regular updates, please register your email here:-
References and credits
To all the online sites and channels.
Pics Courtesy: Internet
Disclaimer:
Information and data included in the blog are for educational & non-commercial purposes only and have been carefully adapted, excerpted, or edited from reliable and accurate sources. All copyrighted material belongs to respective owners and is provided only for wider dissemination.
References:-
- Financial Times, “Russia’s Hybrid Playbook Targets NATO’s Weak Spots”, Dec 2024.
- Financial Times, “Why Underwater Cables in the Baltic Sea Are Vital and Vulnerable”, Jun 2025.
- Reuters, “Baltic Governments Strengthen Cyber Defence Amid Hybrid Threats”, Apr 2025.
- Chivvis C. S, “Understanding Russian Hybrid Warfare and What Can Be Done About It”, Santa Monica, CA: RAND Corporation, 2017.
- European Council on Foreign Relations, “Russian Influence and Hybrid Strategies in the Baltic Sea Region”, Policy Brief, 2023.
- Kasekamp A, “Baltic Security Strategy Report”, Tallinn: International Centre for Defence and Security (ICDS), 2019.
- Åtland K, “Russia’s Hybrid Warfare and the Baltic States: An Assessment of Threats and Responses”, Journal of Slavic Military Studies, 36(2), 123–145, 2023.
- Bērziņa I, “The Baltic States’ Response to Russian Hybrid Threats”, Defence Studies, 22(3), 345–367, 2022.
- Berzins J, “The Baltic Security Dilemma: Hybrid Threats and NATO’s Response”, Riga: Latvian Institute of International Affairs, 2024.
- Clark, D. & Hakala, E, “Submarine Cable Security in the Baltic Sea: Vulnerabilities and NATO’s Role”, NATO Review, 15(4), 1–12, 2023.
- Galeotti M, “Hybrid War and Little Green Men: How It Works and How to Counter It,” The Journal of Slavic Military Studies, 29(3), 401–423, 2016.
- Kofman M. & Rojansky M, “Russia’s Hybrid Warfare Toolkit: Lessons from the Baltics and Ukraine”, Foreign Affairs, 102(5), 78–90, 2023.
- Pynnöniemi K. & Saari S, “Russia’s Information Warfare in the Baltic States: Actors, Tools, and Impacts”, Helsinki: Finnish Institute of International Affairs, 2022.airs, 2022.