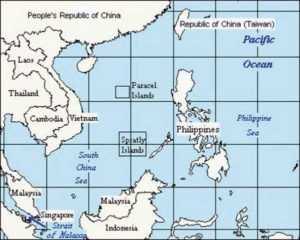
The SCS dispute took root in pre-colonial era and has changed form in the colonial times, decolonization period, Cold War era, and then in more recent times.
Over the years, the dispute has become more complicated by the competing and overlapping claims of several littoral states and involvement and interest of other members of the international community.
Several efforts have been made by regional and global players to resolve the issue bilaterally and / or multilaterally.
China Factor
China uses folklore, myths and legends as well as distorted history to support its territorial and maritime claims in the SCS.
China’s territorial and sovereignty claims have a high degree of ambiguity. Under this umbrella of ambiguity China has been using different methods to pursue its objectives in the SCS following strategy of increased assertiveness while delaying resolution to bid time.
China has been engaging littoral states in bilateral negotiations and holding dialogue with ASEAN but with no breakthrough. At the same time Beijing is increasing its presence in the SCS through naval exercises and physical installations, such as land reclamations and building artificial islands.
China is following its tactics of salami slicing in SCS as well, i.e. making gains without resorting to direct military engagement or confrontation.
Other Claimants
Other claimant states besides China are Taiwan, Philippines, Vietnam, Malaysia, and Brunei. Indonesia is also getting sucked into the dispute.
The claims and stance by these claimant states depends upon factors like identity crisis (Taiwan), rising China and individual political and economic ties with China.
ASEAN
ASEAN has been involved in the conflict management with China to find an amicable solution.
So far ASEAN has been unable to achieve an amicable agreement. Possible reasons are China’s insistence on a bilateral solution and competing claims among claimant states.
July 2016 Arbitration
Status quo on the SCS has not changed significantly after the July 2016 Arbitration, and is not likely to bring any significant change in the near future.
China ignores the arbitral ruling and continues to maintain its intransigence behaviour with no intention to fulfil its international obligation.
Other Players
There are other regional and global players, which are not direct claimants in the SCS dispute but are involved.
Like any other security issue the international community is divided on the question of the SCS disputes. While some countries support one of the sides, others remain neutral.
USA. Role of US is important for the dispute and the region, because it is the only power that is capable of standing up to and counterbalancing the increasing assertiveness of China. US maintains that it does not support the sovereignty claim of any particular state while demanding freedom of navigation and over flight in international waters.
QUAD. The US concern is shared by some of the countries such as Australia, Japan and India giving rise to Quad, which has the potential to bring stability in the region. While the Quad demands peaceful resolution of the SCS dispute and respect for international law, it still remains a dialogue forum rather than a security alliance.
Coming UP: Solving SCS Disputes
Comments and value additions are most welcome
For regular updates please register here –
https://55nda.com/blogs/anil-khosla/subscribe/
References:
- https://scroll.in/article/968918/how-did-the-south-china-sea-dispute-begin-and-where-is-it-headed
- https://www.bbc.com/news/world-us-canada-53397673
- https://www.lowyinstitute.org/issues/south-china-sea
- https://www.peacepalacelibrary.nl/library-special/south-china-sea-territorial-disputes/
- https://www.drishtiias.com/daily-updates/daily-news-analysis/south-china-sea-dispute
- https://www.straight.com/news/khalid-zaka-a-summary-of-south-china-sea-conflict
-
The Politics of South China Sea Disputes, book by Nehginpao Kipgen