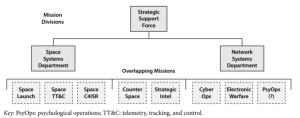
Pic courtesy: strategicstudyindia.blogspot.com.webp
Q 1. Does bringing together the capabilities in space, cyber, electronic and information domains under PLASSF, provide an edge to China through greater civil-military integration?
- It is a good concept and, it gives an advantage to China for the conduct of operations in these four new and important domains (Cyber, Space, Electronic and Information).
- These domains are intrinsically interconnected and should not be dealt with in isolation.
- It enhances the capability even for grey zone warfare (China has mastered the art and uses anything and everything as a weapon).
- Even USA is studying this model for its reorganisation.
- The Chinese model gives us a preview of future warfare challenges.
- More than Civil-Military fusion it streamlines defensive and offensive operations in these domains.
- It ensures seamless operations in the overlapping areas of these domains.
- It has both support and active function.
- It provides support to the service HQs and the theatre commands.
Q2. What are your views about the formation of JSSF and its progress?
- It was formed in 2015 and work is still in progress.
- A Building block methodology has been adopted for it.
- Initially, existing structures were reorganised, giving some new charters to them.
- Thereafter, new structures were added.
- Besides, the military and even some of the civil organisational structures were included in it.
- Operating in expeditionary mode is still a challenge.
- It still has lots of challenges that are being dealt with and the whole concept is evolving.
- It is being exercised during training and live situations, and the lessons learnt are being implemented to make it a viable and efficient service.
Q3. How would the service (JSSF) be used during hostilities?
- Intelligence and information gathering and analysis is a continuous process.
- It would also be used during peacetime for grey zone covert operations with some degree of deniability.
- It would also be used during tense situations for strategic coercion.
- During hostilities, the trend these days is to initiate war with disruptive operations to create chaos. This is followed by attacks by long-range precision vectors to disrupt command, control and communications, adding to the chaos. Kinetic contact force is applied in the prevailing chaotic environment.
- The targets for offensive action in these domains would include ISR capabilities (especially space-based surveillance), military command and control centres and networks, and networks of national importance in sectors like railways, power, banking, health, maritime domain, transportation etc.
- Information warfare would be used to influence the minds of decision-makers in particular and the general public at large.
- The extent of effect (degradation) would depend upon several factors like defensive capability and measures, existing architecture providing alternatives and redundancy, and ability to recoup etc.
- JSSF will provide support (Intelligence and information) and carry out offensive and defensive actions in all four domains, throughout the period of hostilities.
Q4. Do you think China will succeed in building a credible narrative against India, using JSSF and media campaigns (print, electronic, social media), and will such propaganda affect the morale of our defence forces and the civilian population?
- China believes in and follows the three-war theory.
- Media and info war to create a false narrative is a very common practice and China would try.
- It also believes in twisting history to its advantage and creating doctored documents to support its narrative.
- China generally creates two narratives, one for domestic consumption and the other for international use.
- Three major factors in our favour are the high morale of our forces, the high degree of legitimacy of actions by India, and the high nationalistic/patriotic feelings of the general public and citizens.
- Due to the reasons, covered above, the effect will be minimal.
- Even the civilian population can see through the Chinese design and would not get waylaid.
- At the moment the credibility of China in the world is low, and in my opinion, China may not succeed in its endeavour.
- However, it would be prudent to be ready for it and take some proactive steps.
- International opinion is another area to look at.
Q5. What remedial measures need to be implemented to mitigate the threats emerging from this service (JSSF) of PLA?
- The threat of offensive action exists in all four domains.
- Not only the military but a whole government approach (All the stakeholders) would be required.
- It would have to be dealt with at three levels, individual service and stakeholder, at the tri-service level and sector/zone level and the national level.
- Besides fortification of our systems and networks by firewalls and other security features, a Multi-pronged approach is required.
- A multi-layered defence system is required.
- It is not a one-time fix but requires continuous monitoring and upgrades.
- A multi-domain monitoring system is needed.
- A round-the-clock operating, operations room would have to be set up.
- In addition, a Quick Reaction Team concept is required at different levels to contain the effects of any attack.
- An audit and research structure would help in identifying weak areas, vulnerabilities, new developments, and future challenges.
- A Proactive Approach (using electronic, print and cyber media) to counter adverse propaganda.
- Development of counter-offensive capabilities.
Bottom Line
The nature of warfare is changing at a very fast pace.
Adapt or Perish
Question
Are our proposed changes future looking?
Suggestions and value additions are most welcome
For regular updates, please register here
Subscribe
References and credits
To all the online sites and channels.
Disclaimer:
Information and data included in the blog are for educational & non-commercial purposes only and have been carefully adapted, excerpted, or edited from sources deemed reliable and accurate. All copyrighted material belongs to respective owners and is provided only for purposes of wider dissemination.


